Many major companies, like Air Canada, Hollister and Expedia, are recording every tap and swipe you make on their iPhone apps. In most cases you won’t even realize it — or ask for permission.
You can assume that most apps are collecting data on you. Some even monetize your data without your knowledge. But TechCrunch has found several popular iPhone apps, from hoteliers, travel sites, airlines, cell phone carriers, banks and financiers, that don’t ask or make it clear — if at all — that they know exactly how you’re using their apps.
Worse, even though these apps are meant to mask certain fields, some inadvertently expose sensitive data.
Apps like Abercrombie & Fitch, Hotels.com and Singapore Airlines also use Glassbox, a customer experience analytics firm, one of a handful of companies that allows developers to embed “session replay” technology into their apps. These session replays let app developers record the screen and play them back to see how its users interacted with the app to figure out if something didn’t work or if there was an error. Every every tap, button push and keyboard entry is recorded — effectively screenshotted — and sent back to the app developers.
Or, as Glassbox said in a recent tweet: “Imagine if your website or mobile app could see exactly what your customers do in real time, and why they did it?”
The App Analyst, a mobile expert who writes about his analyses of popular apps on his eponymous blog, recently found Air Canada’s iPhone app wasn’t properly masking out the session replays when they were sent, exposing passport numbers and credit card data in each replay session. Just weeks earlier, Air Canada said its app had a data breach, exposing 20,000 profiles.
“This gives Air Canada employees — and anyone else capable of accessing the screenshot database — to see unencrypted credit card and password information,” he told TechCrunch.
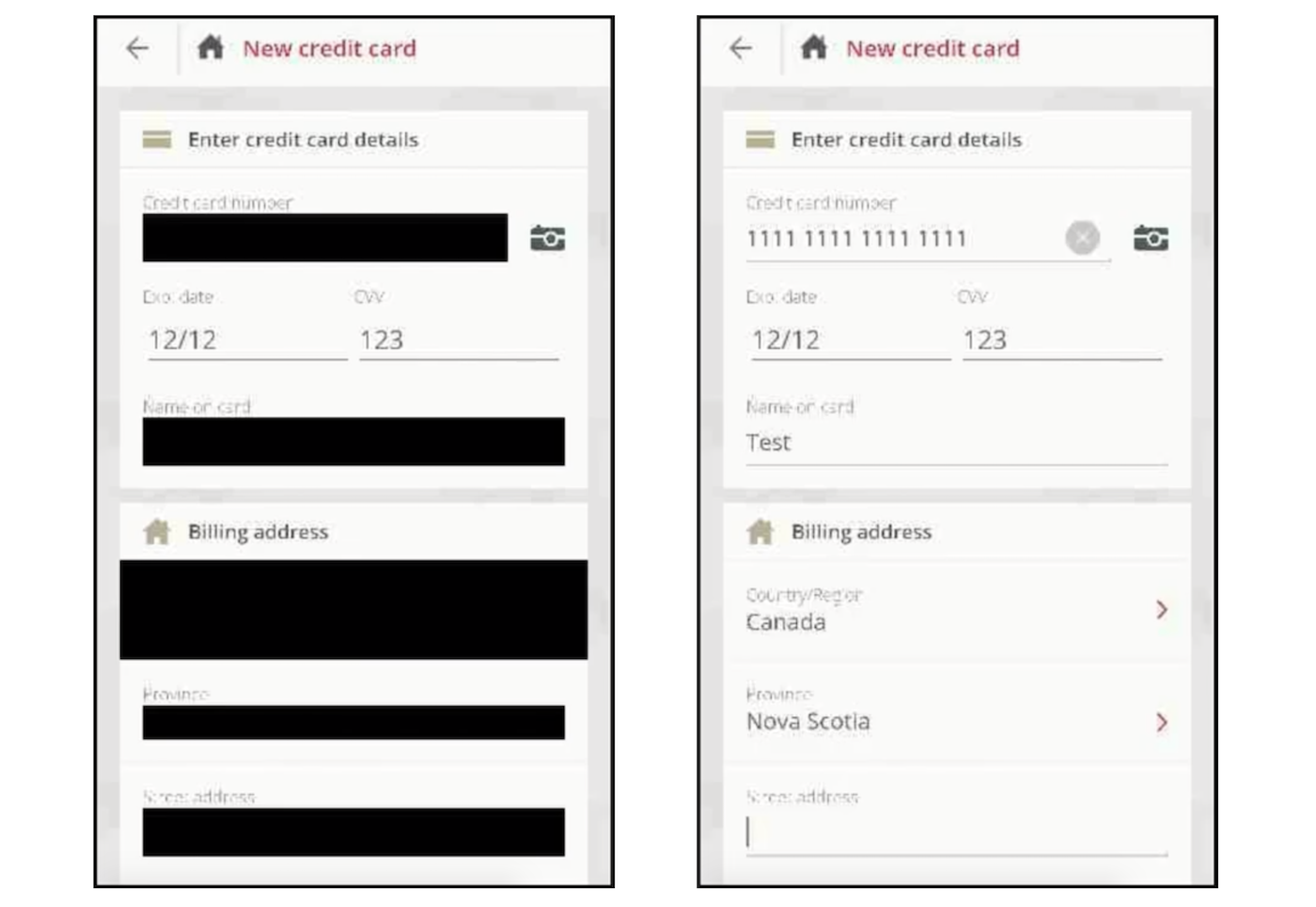
In the case of Air Canada’s app, although the fields are masked, the masking didn’t always stick. (Image: The App Analyst/supplied)
We asked The App Analyst to look at a sample of apps that Glassbox had listed on its website as customers. Using Charles Proxy, a man-in-the-middle tool used to intercept the data sent from the app, the researcher could examine what data was going out of the device.
Not every app was leaking masked data, none of the apps we examined said they were recording a user’s screen — let alone sending them back to each company or directly to Glassbox’s cloud.
That could be a problem if any one of Glassbox’s customers aren’t properly masking data, he said in an email. “Since this data is often sent back to Glassbox servers I wouldn’t be shocked if they have already had instances of them capturing sensitive banking information and passwords,” he said.
The App Analyst said that while Hollister and Abercrombie & Fitch sent their session replays to Glassbox, others like Expedia and Hotels.com opted to capture and end session replay data back to a server on their own domain. He said that the data was “mostly obfuscated,” but did see in some cases email addresses and postal codes. The researcher said Singapore Airlines also collected session replay data but sent back to Glassbox’s cloud.
Without analyzing the data for each app, it’s impossible to know if an app is recording a user’s screens of how you’re using the app. We didn’t even find it in the small print of their privacy policies.
Apps that are submitted to Apple’s App Store must have a privacy policy, but none of the apps we reviewed make it clear in their policies that they record a user’s screen. Glassbox doesn’t require any special permission from Apple or from the user, there’s no way a user would know.
Expedia’s policy makes no mention of recording your screen, nor does Hotels.com’s policy. And Air Canada’s case, we couldn’t spot a single line in its iOS terms and conditions or privacy policy that suggests the iPhone app sends screen data back to the airline. And, in Singapore Airlines’ privacy policy, there’s no mention either.
We asked all of the companies to point us to exactly where in its privacy policies that permit each app to capture what a user does on their phone phone.
Only Abercombie responded, confirming that Glassbox “helps support a seamless shopping experience, enabling us to identify and address any issues customers might encounter in their digital experience.” The spokesperson pointing to Abercrombie’s privacy policy makes no mention of session replays, neither does its sister-brand Hollister’s policy.
“I think users should take an active role in how they share their data, and the first step to this is having companies be forthright in sharing how they collect their users data and who they share it with,” said The App Analyst.
When asked, Glassbox said it doesn’t enforce its customers to mention its usage in their privacy policy.
“Glassbox has a unique capability to reconstruct the mobile application view in a visual format, which is another view of analytics, Glassbox SDK can interact with our customers native app only and technically cannot break the boundary of the app,” the spokesperson said, such as when the system keyboard covers part of the native app/ “Glassbox does not have access to it,” the spokesperson said.
Glassbox is one of many session replay services on the market. Appsee actively markets its “user recording” technology that lets developers “see your app through your user’s eyes,” while UXCam says it lets developers “watch recordings of your users’ sessions, including all their gestures and triggered events.” Most went under the radar until Mixpanel sparked anger for mistakenly harvesting passwords after masking safeguards failed.
It’s not an industry that’s like to go away any time soon — companies rely on this kind of session replay data to understand why things break, which can be costly in high-revenue situations.
But for the fact that the app developers don’t publicize it just goes to show how creepy even they know it is.
Got a tip? You can send tips securely over Signal and WhatsApp to +1 646-755–8849. You can also send PGP email with the fingerprint: 4D0E 92F2 E36A EC51 DAAE 5D97 CB8C 15FA EB6C EEA5.

from iPhone – TechCrunch https://tcrn.ch/2Dcek24